Every Configuration Item within Flow maintains its own security list. This security list determines the rights that any particular user account has for the configuration item.
A user's rights are determined based on the collective result of security assigned to users/groups that the current person belongs to. A windows user group can be assigned as a Flow user so for the purpose of this page we will refer to a user or group as a Windows User.
If a person is logging in using Windows Authentication then they may in fact belong to several groups that have been assigned as Windows Users in Flow. In this case the resulting security for that person is the collective security of all the groups that person belongs to.
When determining the resulting user right a "Denied" flag overrides all other settings. If any user/group that a person belongs to has a denied permission then the resulting security right is denied.
If no security permissions have been assigned then ALL users will have access to the configuration item. By default when creating a new configuration item it will not have any security permissions
User security is best explained with an example. The following screen shot shows user security applied to a DB Connection. The window looks similar no matter what configuration item the security is being applied to.
The following security rights can be applied to a user account. For each of the rights a user account can either be Allowed or Denied. Denied user rights override all other settings regardless of the settings of other groups the user may belong to.
SecurityCancel to close the window without changes, or click Save to close the window and save any changes you have made
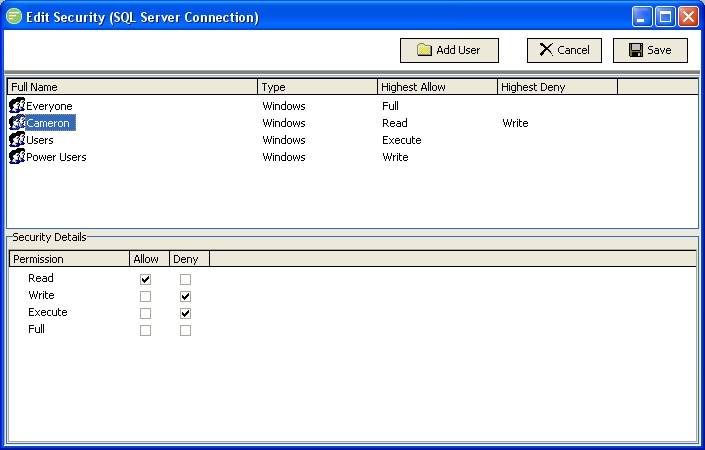
The above Edit Security window shows the list of users with permissions assigned to the configuration item (in this case a DB Connection). The window has the "Cameron" user selected and the details of this user are display in the bottom half of the window.
In the above example the Cameron user is also a member of the Users and Power Users group. The resulting permissions for the Cameron user are therefore the ability to Read (View) the configuration object, but he is denied the ability to Write (Edit) or Execute the item. This is the case even though the Users and Power Users group, of which Cameron is a member, have the ability to Write and Execute the item. Because he is specifically Denied he will not get this right even though other groups he belongs to do. Any other user account that is a member of the Users or Power Users group that is not Cameron will have the ability to Write and Execute the item.